OPENING QUESTIONS: Why is ALL OF THIS necessary for every data layer for every packet that flies out of your router?
OBJECTIVES:
- I will be able to contrast public key encryption with private key encryption during today's class
WORDS FOR TODAY:
certificate:
public key:
private key:
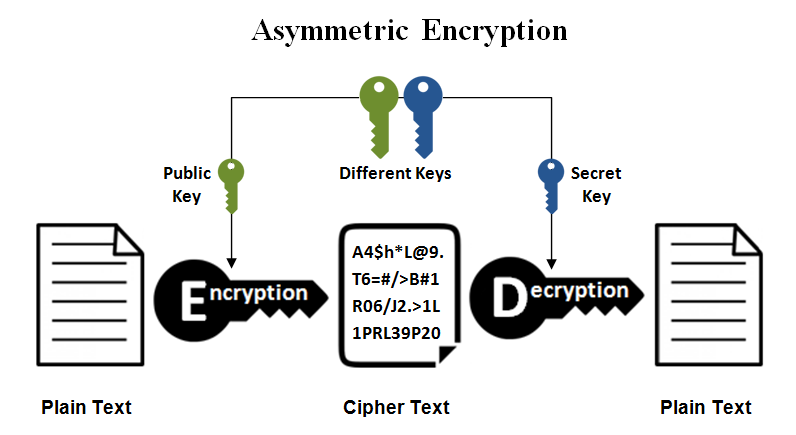
asymmetric encryption: 1 key used to lock (the public key) and 1 key to unlock (private key)
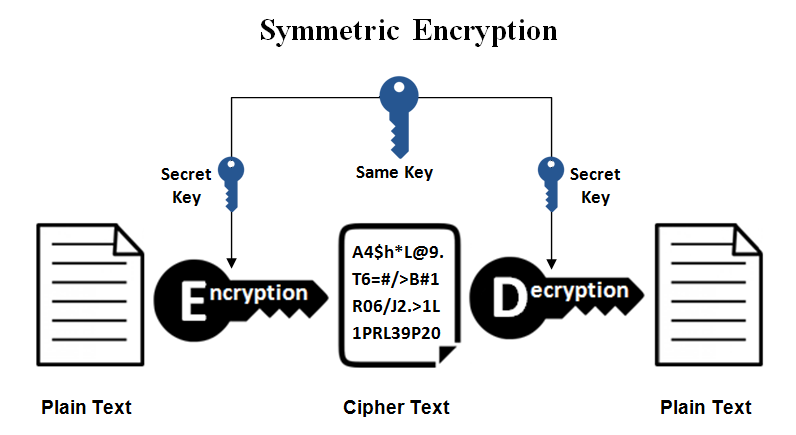
symmetric encryption: 1 key used to lock AND unlock
WORK FOR TODAY:
HERE is my conversation with gpt
- Here's an intriguing question (I hope?): If AES goes through all of that *obfuscation* (there's a good word!), how does the remote computer un-encrypt your data layers? After all, you may have never (and provably never will) communicated with that website and arranged things like secret keys? Please discuss!
In a moment I'm going to turn you lose to work with your team to START the somewhat gentle process of EXPLAINING synchronous encryption. That will be the first step before we dive into the wonderful/complex world of asynchronous encryption (gulp!)
You will come across lots and lots and lots of "simple" images and descriptions that look like this:
So far so good, work with your team to delve into the shared key scenario (it's fairly basic and should go quickly)
Now we're going to dip our toes into the GNARLY DUDE! but fascinating world of asynchronous keys. That we use everytime we connect to an HTTPS site which is... what?
The answer is *gulp* Public Encryption.
That is often 'explained' through much to oversimplified graphics like this:
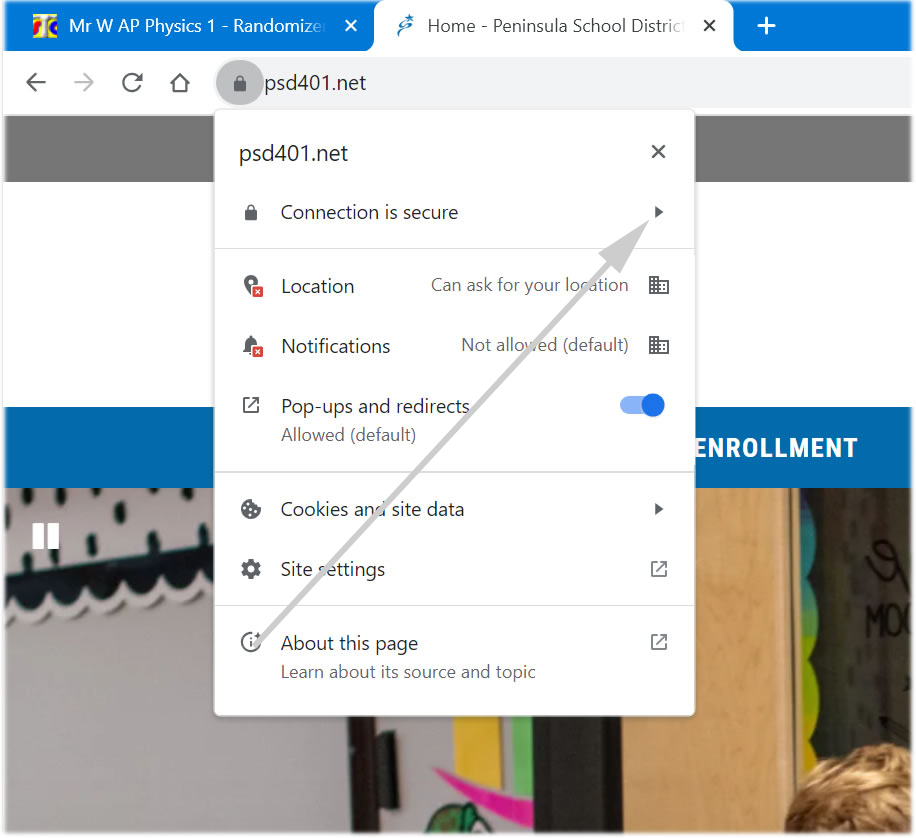
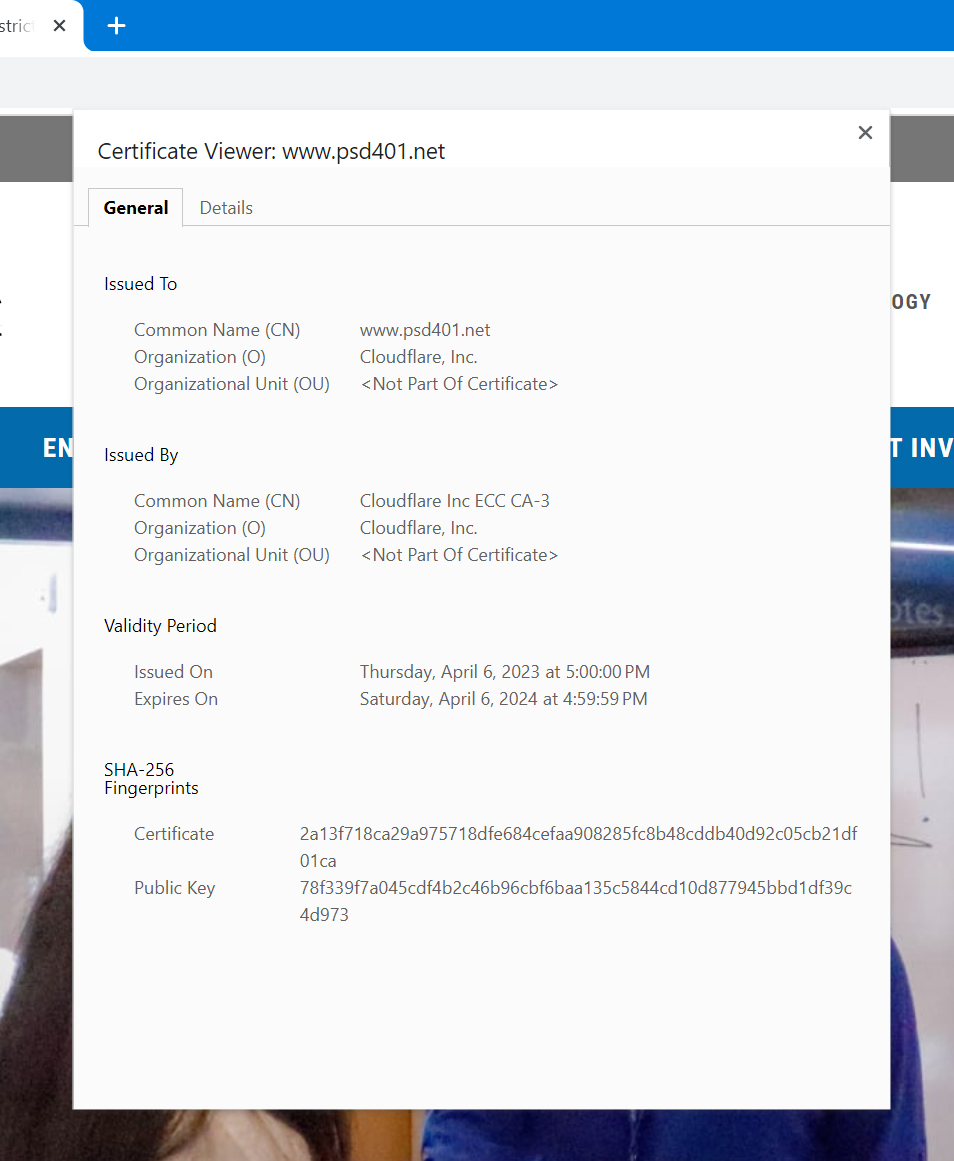
Let's go and take a gander at the public key used for the PSD401.net site to keep that secure!
Thusly!:
Then go here:
What is a "certificate"?
Why on Earth would PSD publish the encryption key for the whole world to see????